Even before the global pandemic hit us, the trend toward remote work was already on the rise. Two kinds of remote workers fueled this trend: regular employees whose companies allow them to work from home several times a week, and individuals who strike out on their own as freelancers.
- Blog
- Sales 800-985-9365
- Support 800-985-9368
Blogs
Want to know about the latest technology news, tips, and trends? You’ve come to the right place
Zoom tips: How to prevent unwanted people from crashing your events

Because of the pandemic, many housebound New Jerseyans have turned to teleconferencing applications for work and for socializing. One of the fastest to, pardon the pun, zoom up the ranks of popularity is Zoom.
Founded in 2011, Zoom is a teleconferencing service that offers video conferencing, mobile collaboration, online meetings, and chat.
Security tips: How your staff can avoid COVID-19-related cyberscams

The COVID-19 pandemic is the most pressing concern affecting all Americans these days. For us in New Jersey, this pandemic hits even closer to home, given that New York is now the epicenter of the outbreak. Because of this, most businesses in the Hanover, Morristown, and Madison areas now have employees working from home, relying heavily on the internet for work and for socializing.
Advantages and disadvantages of remote work during a viral outbreak

More and more businesses are implementing remote work because of its numerous benefits. Boost in productivity, access to a wider pool of talent, and lower operating costs are some that immediately come to mind.
But for many small- or medium-sized business (SMB) leaders, deciding whether to stick to an office-based setup and integrating a remote workforce is hardly black and white, especially now during the COVID-19 outbreak.
The menace of insider threats

Today, the risk posed by having sensitive information leaked to the wrong hands is pervasive. Technology has made the storage, accessibility, and shareability of information greater than ever, but the possibility of that information being made available to parties or entities they were not intended for is similarly increased.
“The best defense is a good defense” and other cliche cybersecurity tips that are actually useful

The best defense is a good defense. Leave nothing to chance. Expect the unexpected. Better safe than sorry.
As a small- or medium-sized business (SMB) owner, you must have read countless tips on how to protect your IT systems. You may have been told the same pieces of advice above — these may all sound cliché, but they’re actually good advice.
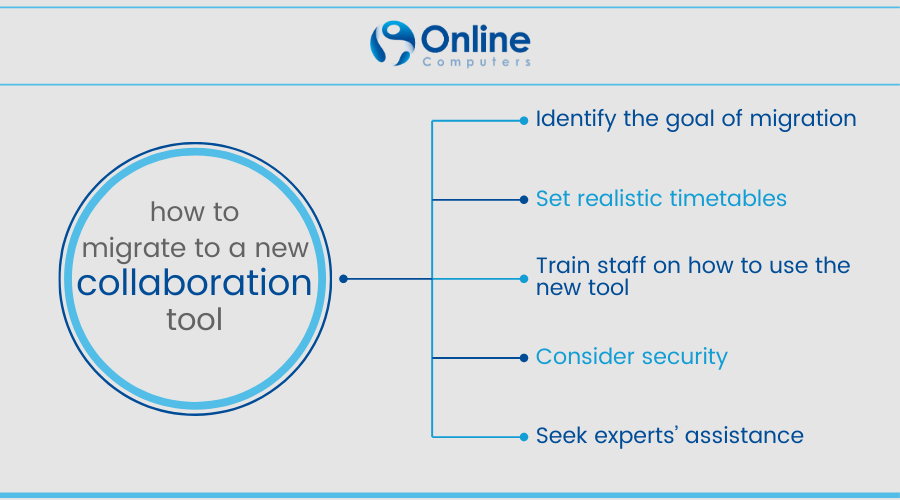
Factors to take into account when migrating to a new collaboration tool
Creating an effective multicloud strategy
Common IT cost-cutting mistakes and how to avoid them

Cost-cutting is inevitable in business. At some point, almost every department in any business will face the need to reduce expenditure while maintaining its functions. This is especially challenging when it comes to IT, where the mix of people, infrastructure, and equipment complicates the matter significantly.
Drones: The new attack vector for malware and cybercriminals

Far from being the novelty item they once were, drones now play an important role in industries like manufacturing, agriculture, and construction. They can be used to survey the land, transport materials, and reach areas inaccessible to people.
However, the fact that they’re primarily used for surveillance means they’re an increasingly popular target for hackers.